Computing Environments:
Computing environments include computer machinery, data storage devices, workstations, software applications, and networks that support the processing and exchange of electronic information demanded by software solutions.
Types of Computing Environments:
A brief discussion of how operating systems are used in various types of computing environments are as follows:
i. Traditional Computing: As computing has matured, the line separating many of the traditional computing environments have blurred. Consider the ‘typical office environment.’ Just a few years ago, it considered PCs connected to a network, with servers providing file and print services. Remote access was awarded and portability was achieved by the use of laptop computers. Terminals attached to the mainframe were prevalent at many companies as well, with even fewer remote access and portability options.
The current trend is toward providing more ways to access these computing environments. Web technologies and increasing one WAN bandwidth are stretching the boundaries of traditional computing. Companies established portals, which provide web access to their internal servers. Network computers are essentially terminals that understand web-based computing which used in place of the traditional workstation where more security or easier maintenance is desired.
ii. Mobile Computing: Mobile computing refers to computing on handheld smartphones and tablet computers. These device distinguishing physical features of being portable and lightweight. Historically, compared with desktop and laptop computers, mobile systems gave up screen size, memory capacity, and overall functionality in return for handheld mobile access to services such as email and web browsing. Over the past few years, however, features of mobile devices have been so rich that the distinction in functionality between, say, a consumer laptop and a tablet computer may be difficult to discern. In fact, we might argue that the features of a contemporary mobile device allow it to provide functionality that is easier unavailable or impractical on a desktop or a laptop computer.
Today, mobile systems are used not only for e-mail and web browsing but also for playing music and video, reading digital books, taking photos, and recording high-definition video. Two operating systems currently dominate mobile computing: Apple iOS and Google Android. iOS was designed to run on Apple iPhone and iPad mobile devices. Android powers smartphones and tablets computers available from many manufactures.
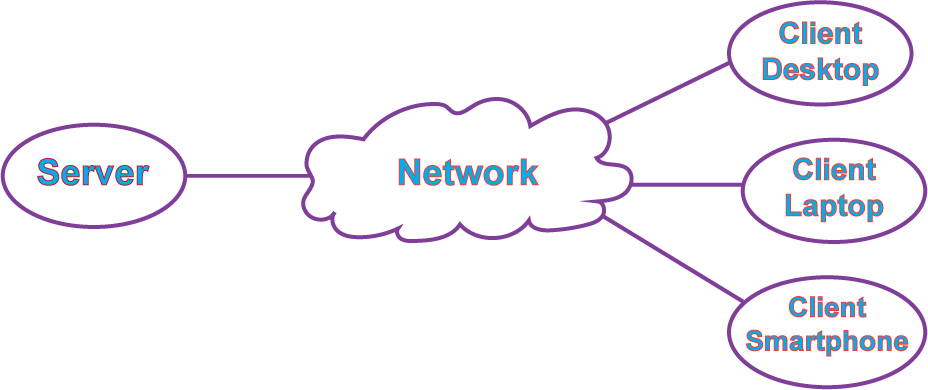
iii. Distributed Systems: A distributed system is a collection of physically separate, possibly heterogeneous, computer systems that are networked to provide users with access to the various resources that the systems maintain. Access to a shared resource increases computation speed, functionality, data availability, and reliability. Some operating systems generalize network access as a form of file access, with the details of networking contained in the network interfaces device driver. Others make users specifically invoke network functions. Generally, systems contain a mix of two modes – for example, FTP and NFS.
A network operating system is an operating system that provides features such as file sharing across the network, along with a communication scheme that allows a different process on different computers to exchange messages. A computer running a network operating system acts autonomously from all other computers on the network, although it is aware of the network and is able to communicate with other networked computers. A distributed operating system provides a less autonomous environment. The different computers communicate closely enough to provide the illusion that only a single operating system controls the network.
iv. Client-Server Computing: As PCs have become faster, more powerful, and cheaper, designers have shifted away from centralized system architecture. Terminals connected to centralized systems are now being supplanted by PCs and mobile devices. Server systems can be broadly categorized as compute servers and file servers:
- The computer-server system provides an interface to which a client can send a request to perform an action (for example, read data). In response, the server executes the action and sends the results to the client. A server running a database that responds to client requests for data is an example of such a system.
- The file-server system provides a file-system interface where clients can create, update, read, and delete files. An example of such a system is a web server that delivers files to clients running web browsers.
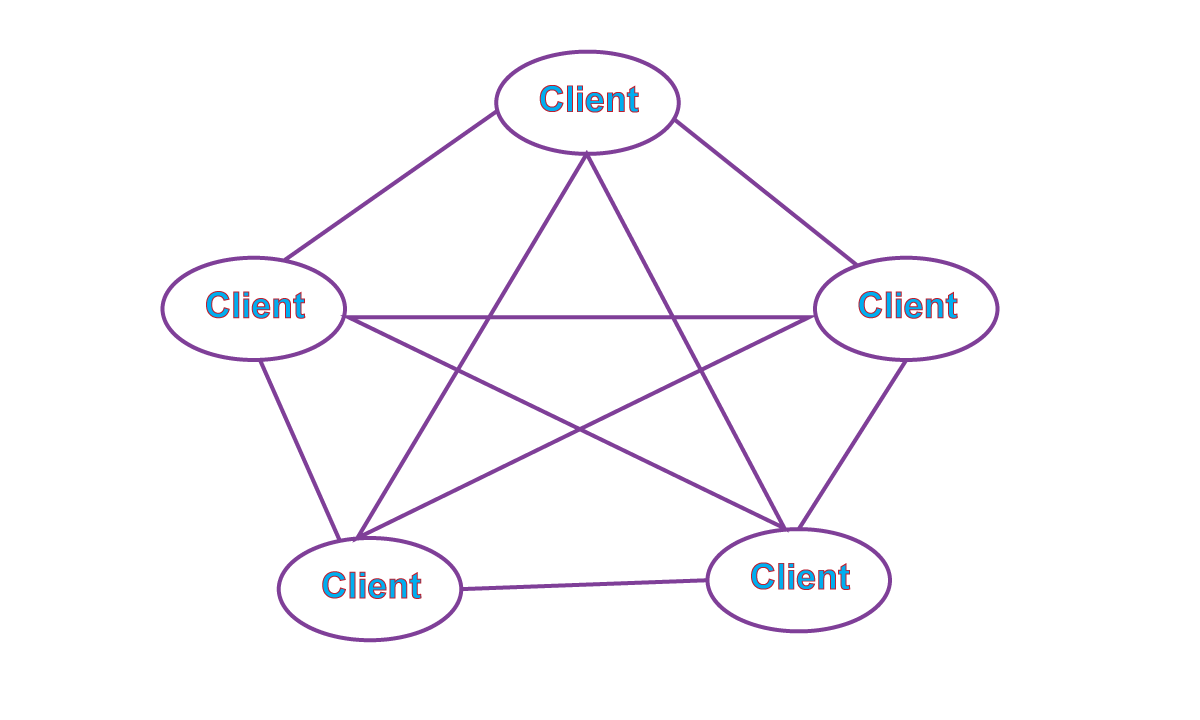
v. Peer-to-Peer Computing: Another structure for a distributed system is the peer-to-peer (P2P) system, model. In this method, clients and servers are not distinguished from one another. Peer-to-peer systems offer an advantage over traditional client-server systems and services can be provided by several nodes distributed throughout the network.
To participate in a peer-to-peer system, a node must first join the network of peers. Once a node has joined the network, it can begin providing services to – and requesting services from – other nodes in the network. Determining what services are available is accomplished is one of two general ways:
- When a node joins a network, it registers its services with a centralized lookup service on the network. The remainder of the communication takes place between the client and the server provider.
- An alternative scheme uses no centralized lookup service. Instead, a peer acting as a client must discover what node provides the desired service by broadcasting a request for the service to all other nodes in the network. The node (or nodes) providing that service responds to the peer making the request. A discovery protocol must be provided that allows peers to discover services provided by other peers in the network.
Skype is an example of peer-to-peer computing. It allows clients to make voice calls and video calls and to send text messages over the internet using a technology known as voice over IP (VoIP). It includes a centralized login server, but it also incorporates decentralized peers and allows two peers to communicate.
vi. Virtualization: Virtualization is a technology that allows operating systems to run as applications within other operating systems. The virtualization industry is vast and growing, which is a testament to its utility and importance.
Broadly speaking, virtualization is one member of a class of software that also includes emulation. Emulation is used when the source CPU type is different from the target CPU type. A common example of emulation occurs when a computer language does not comply with native code but instead is either executed in its high-level form or translated to an intermediate form.
vii. Cloud Computing: Cloud Computing is a type of computing that delivers computing storage and even applications as a service across a network. There are actually many types of cloud computing, including the following:
- Public Cloud – a cloud available via the internet to anyone willing to pay for the services.
- Private Cloud – a cloud run by a company for that company’s own use.
- Hybrid Cloud – a cloud that includes both public and private cloud components.
- Software as a service (SaaS) – one or more applications (such as word processors or spreadsheets) available via the internet.
- Platform as a service (PaaS) – a software stack ready for application use via the internet (for example, a database server).
- Infrastructure as a service (IaaS) – servers or storage available over the internet (for example, storage available for making backup copies of production data).
viii. Real-Time Embedded Systems: Embedded computers are the most prevalent form of computers in existence. These devices are found everywhere, from car engines and manufacturing robots DVDs and microwave ovens. They tend to have very specific tasks. The systems they run on are usually primitive, and so the operating systems provide limited features. Usually, they have little or no user interface, preferring to spend their time monitoring and managing hardware devices, such as automobile engines and robotic arms.
The use of embedded systems continues to expand. It almost runs a real-time operating system. A real-time system is used when rigid time requirements have been placed on the operation of the processor or the flow of data, it is often used as a control device in a dedicated application. A real-time system functions correctly only if it returns the correct result within its time constraints.
Reference: Operating System Concepts written by Abraham Silberschatz, Peter Baer Galvin, and Greg Gagne.

Former Student at Rajshahi University