Information security is a critical component of modern organizations’ strategic initiatives, encompassing a multifaceted approach to safeguarding digital assets and data. In an era marked by pervasive digital connectivity and escalating cyber threats, the objectives of information security play a pivotal role in ensuring the trustworthiness, availability, and confidentiality of sensitive information.
What is Information Security?
Information security, often referred to as cybersecurity, is the practice of protecting information from unauthorized access, disclosure, alteration, and destruction. It involves implementing measures and strategies to safeguard digital and physical information assets, ensuring confidentiality, integrity, and availability. For example; encrypting sensitive data to prevent unauthorized users from accessing or understanding it, thereby maintaining confidentiality.
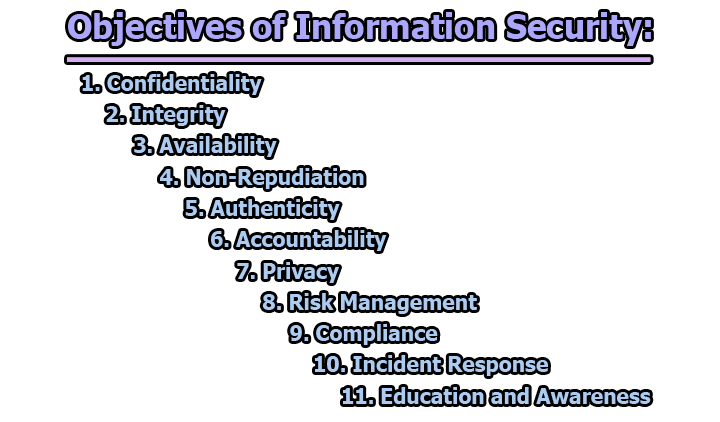
Objectives of Information Security:
1. Confidentiality: Confidentiality in information security ensures that sensitive data is accessible only to authorized individuals or entities. It involves preventing unauthorized access, disclosure, or exposure of information.
Organizations employ various measures such as encryption, access controls, and secure communication channels to maintain confidentiality. Encryption transforms data into a form that can only be understood by authorized parties, and access controls restrict users to only the information they are authorized to view. For example, securing financial transactions, personal records, or proprietary business information requires a strong emphasis on maintaining confidentiality.
2. Integrity: Integrity ensures the accuracy and trustworthiness of information by safeguarding against unauthorized alterations, corruption, or tampering.
To maintain integrity, organizations implement techniques like checksums, digital signatures, and version controls. Checksums are used to verify the integrity of files by comparing a computed checksum with a known, trusted value. Digital signatures use cryptographic methods to sign documents, ensuring that the sender is authenticated, and the content has not been altered. For instance, ensuring the integrity of software updates is crucial to prevent the installation of malicious code.
3. Availability: Availability ensures that information and resources are accessible and usable by authorized individuals when needed, without disruptions.
Availability is maintained through practices such as redundancy, backups, and disaster recovery planning. Redundant systems and backups ensure that if one component fails, there is another ready to take over, minimizing downtime. Disaster recovery plans outline steps to be taken in the event of a disruption, ensuring that critical services can be restored swiftly. For example, a robust availability strategy is essential for online services, where downtime can lead to significant financial losses and loss of customer trust.
4. Non-Repudiation: Non-repudiation ensures that individuals cannot deny their actions or transactions, providing proof of their involvement.
Digital signatures, timestamps, and audit logs contribute to achieving non-repudiation. Digital signatures verify the origin and integrity of messages, making it difficult for the sender to deny sending them. Timestamps provide a chronological record of events, making it challenging to dispute the timing of actions. Audit logs capture and store user activities, serving as evidence in case of disputes. In legal and financial transactions, non-repudiation is crucial to establish accountability.
5. Authenticity: Authenticity verifies the identity of individuals, systems, or entities, ensuring they are who or what they claim to be.
Authentication methods include passwords, biometrics, and multi-factor authentication. Passwords verify the user’s identity based on a secret code, while biometrics use unique physical or behavioral traits. Multi-factor authentication combines multiple methods for added security. For example, a user accessing a secure system may need to provide a password and a fingerprint scan. Authenticity is fundamental to preventing unauthorized access and ensuring that actions within a system are attributed to the correct entities.
6. Accountability: Accountability in information security involves holding individuals or entities responsible for their actions within an information system. It ensures that actions can be traced back to specific users.
To establish accountability, organizations implement logging and monitoring systems. User activities, system events, and access attempts are logged, allowing administrators to review and analyze them. This information not only helps in identifying security incidents but also aids in audits and compliance checks. For example, accountability measures can be critical in determining the source of a security breach and taking appropriate actions against the responsible party.
7. Privacy: Privacy in information security focuses on safeguarding individuals’ personal information and ensuring compliance with privacy laws and regulations.
Organizations employ privacy-enhancing techniques such as data anonymization, encryption, and access controls. Anonymizing data involves removing or altering personally identifiable information, making it challenging to trace information back to specific individuals. Encryption protects sensitive data during storage and transmission. Access controls limit who can access certain types of information. Compliance with privacy laws like GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act) is essential to protect individuals’ privacy rights.
8. Risk Management: Risk management in information security involves identifying, assessing, and mitigating risks to the confidentiality, integrity, and availability of information assets.
Organizations conduct risk assessments to identify potential vulnerabilities and threats. Once identified, they assess the likelihood and impact of these risks and prioritize them based on their significance. Mitigation strategies may involve implementing security controls, creating contingency plans, or transferring the risk through insurance. Regularly reviewing and updating risk assessments is crucial as the threat landscape evolves. Effective risk management helps organizations make informed decisions to protect their information assets.
9. Compliance: Compliance in information security involves adhering to laws, regulations, and industry standards related to the protection and handling of information.
Organizations must comply with various regulations and standards depending on their industry and geographic location. Examples include GDPR, HIPAA, ISO/IEC 27001, and PCI DSS (Payment Card Industry Data Security Standard). Compliance involves implementing specific security measures, conducting audits, and reporting on adherence to regulations. Failure to comply with these requirements can result in legal consequences, financial penalties, and damage to an organization’s reputation.
10. Incident Response: Incident response in information security involves developing and implementing plans to respond effectively to security incidents and breaches.
Incident response plans outline the steps to be taken when a security incident occurs. This includes detecting and analyzing the incident, containing its impact, eradicating the threat, recovering from the incident, and learning from the experience to improve future response efforts. Having a well-defined incident response plan is crucial for minimizing the damage caused by security incidents and restoring normal operations as quickly as possible.
11. Education and Awareness: Education and awareness in information security involve promoting a culture of security awareness and providing training to users to reduce human-related security risks.
Human factors, such as social engineering and phishing attacks, are common vectors for security breaches. Education and awareness programs aim to inform employees about the risks, teach them how to recognize and respond to security threats, and foster a security-conscious culture within the organization. Regular training sessions, simulated phishing exercises, and communication campaigns contribute to building a workforce that actively participates in the protection of information assets.
In conclusion, the objectives of information security form the cornerstone of a resilient and adaptive defense against the evolving landscape of cyber threats. Confidentiality, integrity, availability, non-repudiation, authenticity, accountability, privacy, risk management, compliance, incident response, and education collectively establish a robust and holistic approach to safeguarding information assets. As organizations continue to navigate the complexities of the digital age, integrating and prioritizing these objectives become indispensable for fostering a culture of security, ensuring regulatory compliance, and fortifying resilience against unforeseen challenges. Information security is not merely a technological necessity but a strategic imperative that underpins the trust and reliability essential for the interconnected and information-driven world we inhabit.

Library Lecturer at Nurul Amin Degree College